Industry 4.0 has encouraged advanced technology in the textile industry. It has influenced OEMs to develop new machines with technologies such as automated monitoring of operations, digital remote access and maintenance, cloud connectivity, condition and energy monitoring, etc.
Earlier, a conventional brownfield factory had no knowledge of connectivity with higher-level IT systems, and a direct connection to the Internet was very rare. Machine builders and operators had no reason to concern themselves with the topic of cybersecurity.
However, with increased connectivity, transferring data from the machine controller to the IT or cloud requires a connection to the Internet. Industrial PCs and other hardware are used as edge devices bridging the IT / OT gap by providing connectivity mechanisms, making it susceptible to cyberattacks. Advanced textile machines with cloud connectivity therefore need enhanced security.
DDoS attacks
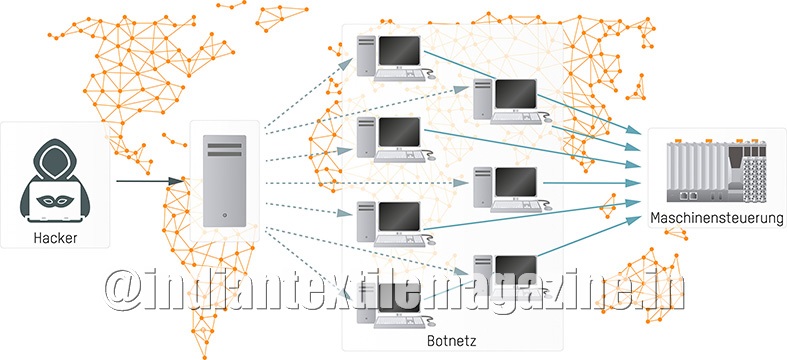
Hackers paralyze controllers and thus the entire machines, for example, by overwhelming them with traffic. This is known as a DDoS (Distributed Denial of Service) attack: A hacker distributes attack programs across a so-called botnet comprising several hundred to a thousand computers, smartphones and tablets, effectively weaponizing them. On command, the bots then bombard a machine controller with so many simultaneous requests that it fails under the load and the machine stops, as demonstrated recently by a malware attack at a microprocessor manufacturer.
Open ports
To transfer data to the cloud, ports must be opened on the machine controller. “As long as the communication channel between the controller and the cloud gateway is open, these ports are an open window for hackers,” says Andreas Hager, Product Manager – Control Systems, B&R. That’s not the only problem, however. Devices that are directly connected to the Internet must be updated regularly to close newly discovered gaps in security.
“Many textile machines run continuously for weeks or more,” notes Hager. Yet, updates can only be installed when the machine is stopped. Following an update, it may even be necessary to adjust the application. “That’s a lot of work, and in the long run simply not a viable answer.”
Luckily, there is a simple solution: the control functionality and communication functionality must be isolated from each other. That way, a DDoS attack would be unable to penetrate deep enough to affect machine control. “In the worst case, you might loose communication with the cloud, but the machine itself can continue to operate,” emphasizes Hager.
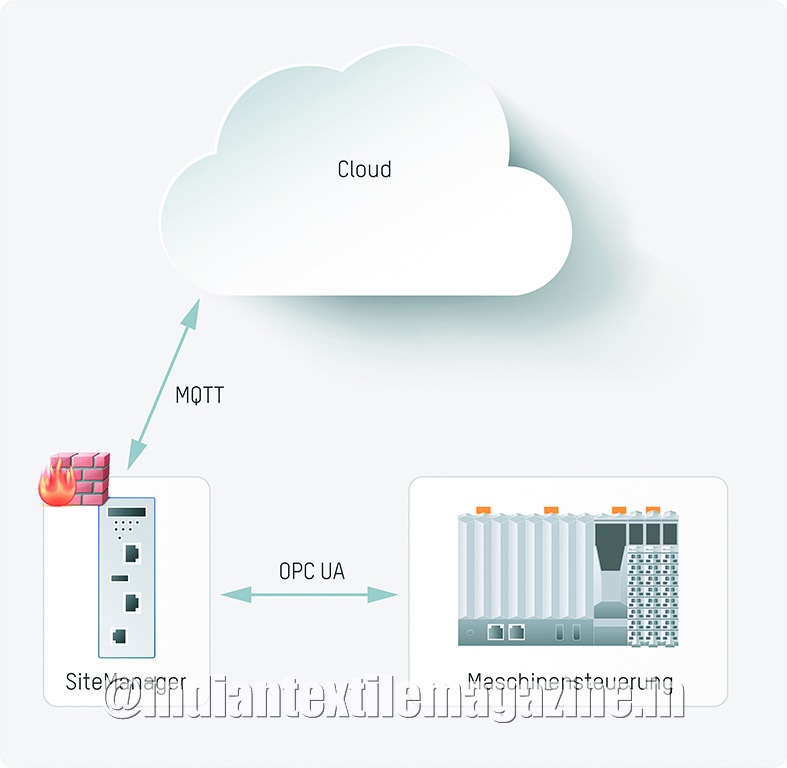
B&R has introduced the SiteManager for this purpose. The device has an integrated firewall and performs all the tasks required for cybersecurity, such as keeping cloud certificates up to date and applying patches to close security holes.
Cloud connectivity
To transfer data to the cloud, the controller connects with the SiteManager via OPC UA. During configuration, the user defines which data is to be transferred. It is also possible to transfer different data to different cloud providers. Configuration is a simple matter of checking boxes in the SiteManager’s web-based user interface.

If a cloud certificate needs to be updated, the machine operator doesn’t have to do anything. The SiteManager automatically downloads and installs updates without affecting machine operation. This also ensures that the security guidelines of the cloud providers are always adhered to and any potential security gaps are closed quickly.
“The security requirements for remote maintenance are very similar to those for cloud communication,” explains Hager. The SiteManager is therefore perfectly suited for this purpose as well.
The device allows service technicians to connect to the machine control system via a secure VPN connection and search for errors. A user management system provides clearly defined and tamper-proof control over which technicians have access to which controllers. “With a technician on site, it is then possible to begin a targeted trouble-shooting process,” says Hager. “The SiteManager ensures that any data transferred between the machine and applications outside the company network are protected against unauthorized access and cyberattacks.”
Edge computing
Edge computing is a method of collecting large volumes of data near its source so that it can be compressed and aggregated before being passed on to higher-level systems. The link between real-time systems at the machine and process level (OT = Operational Technology) and the world of IT is known as an edge device. B&R offers three different types of edge device to cover all applications: Edge Controller, Edge Embedded and Edge Connect.

The B&R SiteManager is available in three variants, providing an Internet connection via LAN, WLAN or mobile network. All the three variants are equipped with an integrated firewall. In order to avoid conflicts with plant firewalls, communication to the Internet is handled using firewall-compatible encrypted web protocols.
In addition to the three hardware variants of the SiteManager, there is also a software version that makes it possible to combine the SiteManager and machine controller in one device. This is made possible by using B&R Hypervisor to install two operating systems on an industrial PC: the real-time operating system for machine control and a Linux or Windows system for the SiteManager. The two operating systems run completely independently of one another. Even if the SiteManager were to be blocked by an attack or the general purpose operating system would crash, machine control would continue unaffected.
“Having the SiteManager between the controller and the cloud ensures that any data transferred between the machine and applications outside the company network are protected against unauthorized access.”
– Andreas Hager, Product Manager – Control Systems, B&R